Handler and Payload
Virtual Handler
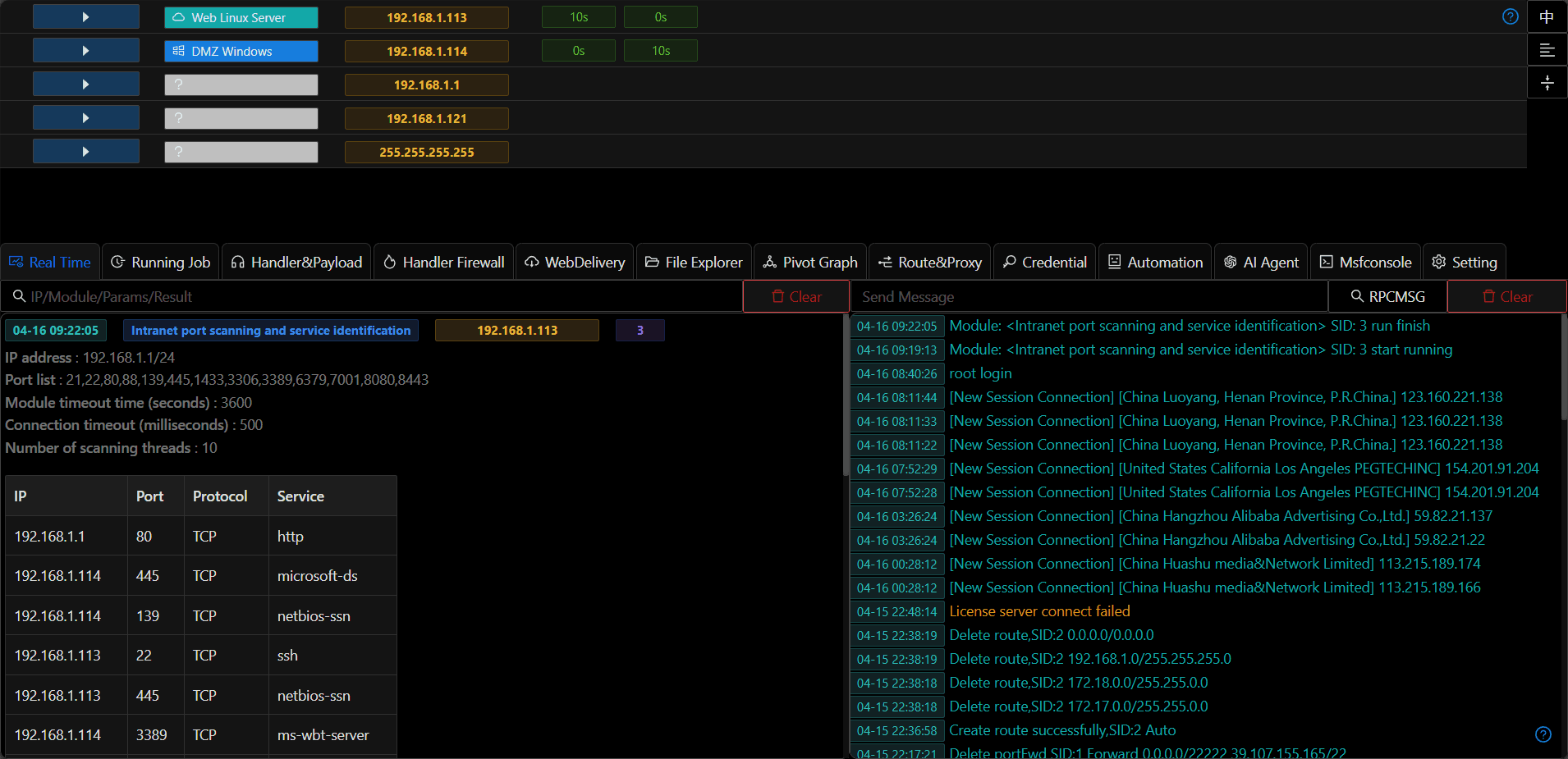
- In certain internal network penetration scenarios (such as shellcode injection, spawn process, AB network forward handler), you may only need to quickly call existing handler configurations without establishing actual network listeners or connections. This can be achieved through creating virtual handlers
- Virtual handlers and real handlers can be converted to each other
- A
virtual handlerrefers to storing the input handler configuration options in cache without establishing an actual running handler on the server. The handler configuration can be quickly selected when running modules/transport protocols later Virtual handlerspersist after system restart and can be used in scenarios such as phishing simulation and persistence- Real handlers are indicated by green icons, while virtual handlers are indicated by gray icons
- Virtual and real handlers can be converted to each other through
To VirtualandTo Realoptions
HTTPS Certificate
- Viper comes with a built-in SSL certificate
www.example.com.pemthat can be used directly for HTTPS encryption. Users can also upload their own PEM format certificates. Note that the certificate must contain both public and private keys. Refer to thewww.example.com.pemfile for the specific format - You can use the module Clone Https Certificate to clone certificates from any website
Generate PE/ELF
- You can quickly generate payloads by clicking the
Generate PE/ELFbutton in the handler
Generate Payload
- Select the
Generate Payloadbutton to manually input configuration to generate payloads - Select the
Auto Handleroption to automatically add the corresponding handler after generating the payload