Parent Process PID Spoofing to Evade Detection
Main Function
The module generates an exe file with a payload. After execution, it automatically migrates to the ie process and spoofs the parent process (PPID) to be explorer.exe (Windows Explorer).
Operation Method
- Open the module, select listen, and run.
- Generate the cpp source code and download it.

- Download the source code and compile it using Visual Studio.
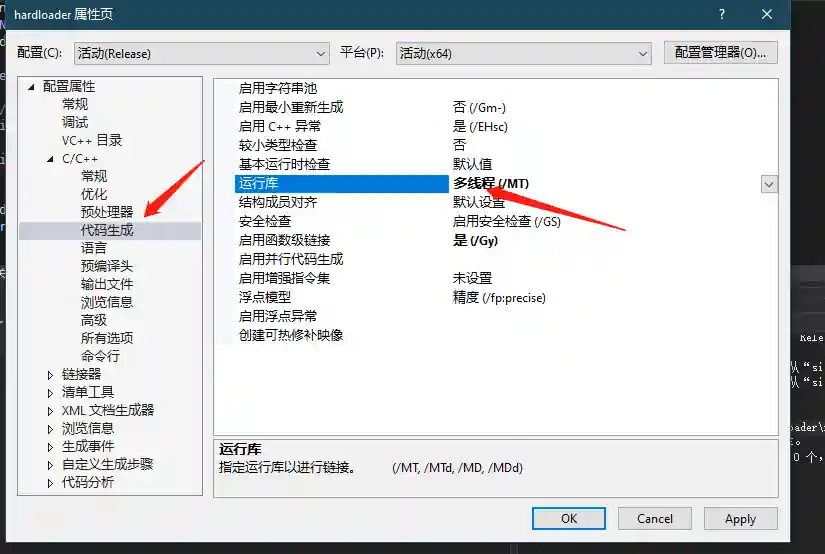
The compiler built into Viper is Mingw64. When compiling this module, the anti - detection effect is poor. Therefore, the source code is provided for users to compile by themselves.

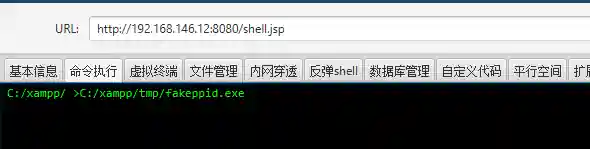
Upload and run it on the target host.
When using a webshell to run the exe generated by this module for connection, the effect is as follows:
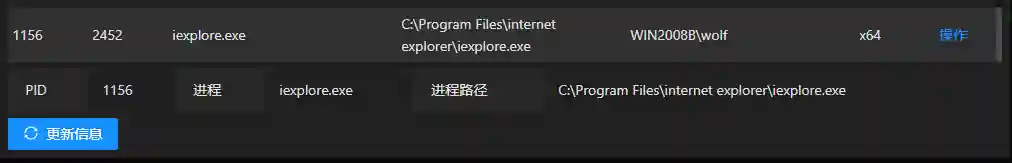
It can be seen that the process of the payload is ie, and the parent process is explorer.exe. This can effectively defend against AV detection and blue - team tracing.
- Comparative test: When using a webshell to run the exe generated by other anti - detection modules for connection, the effect is as follows:
It can be seen that the parent process of the payload is cmd.exe (Behinder).